Understanding Media Access Control (MAC): Key Role in Network Communication
What is Media Access Control (MAC)? An In-Depth Guide
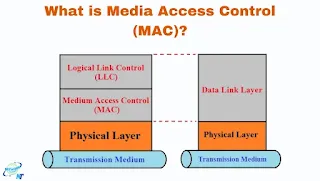
In today’s interconnected world, effective communication between devices within a network is vital. One key element enabling smooth and efficient data transfer across networks is Media Access Control (MAC). The MAC protocol, located within the Data Link Layer (Layer 2) of the OSI model, plays a crucial role in determining how devices on a network communicate and manage the access to the shared transmission medium.
we’ll explore what Media Access Control is, its importance, how it works, and the methods used to ensure seamless communication between networked devices. Additionally, we will examine how MAC addresses function and their significance in modern networking.
Understanding Media Access Control (MAC)
Media Access Control (MAC) refers to the set of rules and protocols used by devices to access and transmit data over a network. MAC is part of the Data Link Layer (Layer 2) in the OSI model, acting as a bridge between the physical layer (hardware) and the network layer (software).
The primary role of MAC is to control how devices within a local network share access to the communication channel. Without effective MAC protocols, network communication could result in data collisions, where multiple devices attempt to send data at the same time, leading to inefficient or failed data transmission.
The MAC protocol helps avoid these collisions, ensuring smooth, reliable, and collision-free data communication. It is essential for Ethernet networks, Wi-Fi networks, and other communication systems.
The Role of MAC in Networking
At its core, MAC provides several important functions:
-
Addressing: MAC assigns a unique address to every device on a network. This unique identifier, called a MAC address, is used to distinguish devices from one another. The MAC address is fixed to the device’s network interface card (NIC), meaning it does not change, providing a consistent way to identify devices within a network.
-
Channel Access Control: MAC determines when and how devices can send data over the shared network medium, preventing multiple devices from transmitting data simultaneously, which could cause a collision.
-
Data Transfer: The MAC layer manages how data packets are sent and received between devices, ensuring the correct transfer of information within the network.
How MAC Addressing Works
A MAC address is a unique 48-bit identifier assigned to a network interface card (NIC). These addresses are typically represented in hexadecimal format, often written as:
-
MM:MM:MM:SS:SS:SS
-
MM-MM-MM-SS-SS-SS
The first half of the MAC address identifies the manufacturer of the device, while the second half is a unique identifier assigned by the manufacturer to that particular network device.
The MAC address operates at Layer 2, unlike IP addresses, which operate at Layer 3 (Network Layer). An easy way to distinguish between the two is to remember that MAC addresses are tied to a device’s physical interface, whereas IP addresses are assigned to a device’s software implementation and can change depending on the network.
Types of Media Access Control Methods
There are several methods used by MAC to avoid data collisions and ensure proper data transmission. These methods are crucial to the smooth operation of networks, especially in high-traffic environments. Here are some of the most commonly used MAC methods:
-
Carrier Sense Multiple Access with Collision Detection (CSMA/CD)
-
Used in: Ethernet networks
CSMA/CD is a method in which a device listens for a signal on the network before transmitting data. If the channel is clear, the device sends its data. If another device sends data simultaneously, causing a collision, both devices wait a random amount of time before trying again.
-
-
Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA)
-
Used in: Wireless networks like Wi-Fi and AppleTalk
CSMA/CA works similarly to CSMA/CD but with a twist. Rather than detecting collisions after they happen, it takes proactive steps to avoid them. This is especially important in wireless networks, where collision detection isn’t feasible due to the physical nature of wireless signals.
-
-
Token Passing
-
Used in: Token Ring and Fiber Distributed Data Interface (FDDI) networks
In token passing, a small data packet (token) is passed around the network. Only the device holding the token can transmit data. This eliminates the risk of collision as only one device can send data at a time.
-
-
Demand Priority
-
Used in: 100BaseVG networks
This method prioritizes access to the network based on demand. Devices with higher priority needs can transmit data more easily than devices with lower priority needs, ensuring that critical data gets through.
-
MAC in Real-World Networking
In real-world applications, MAC is used to identify devices, control data flow, and prevent network congestion. When devices communicate, they use their MAC addresses to ensure the data is sent to the right recipient.
For example, in Ethernet networks, switches use MAC addresses to forward data to the correct device. Layer 2 switches maintain a MAC address table, mapping each device’s MAC address to the corresponding port. When data is sent to the network, the switch uses this table to forward the packet to the correct device.
Additionally, ARP (Address Resolution Protocol) plays a role in translating IP addresses to MAC addresses, ensuring that devices can communicate correctly in an IP network.
The Importance of MAC in Modern Networks
MAC plays an indispensable role in network security, performance, and reliability. Here’s why:
-
Security: MAC addresses help prevent unauthorized devices from accessing the network. By filtering MAC addresses, administrators can ensure that only trusted devices connect to the network.
-
Performance: MAC protocols such as CSMA/CD and CSMA/CA ensure efficient data transmission in environments where many devices share the same communication medium, improving overall network performance.
-
Scalability: As networks grow in size and complexity, the use of MAC addresses and protocols ensures that devices can communicate without interference, even in large-scale systems.
Media Access Control (MAC) is an essential component of modern networking that helps manage how devices access shared communication channels, preventing data collisions and ensuring smooth and efficient data transfer. From Ethernet networks to Wi-Fi and beyond, the MAC protocol plays a pivotal role in how devices communicate and how networks are structured.
Understanding how MAC addressing works, the different MAC access methods, and the importance of MAC in real-world networking allows network administrators to maintain optimal network performance and security. As the backbone of local and wide-area networks, MAC remains a critical piece of the puzzle in today’s interconnected world.